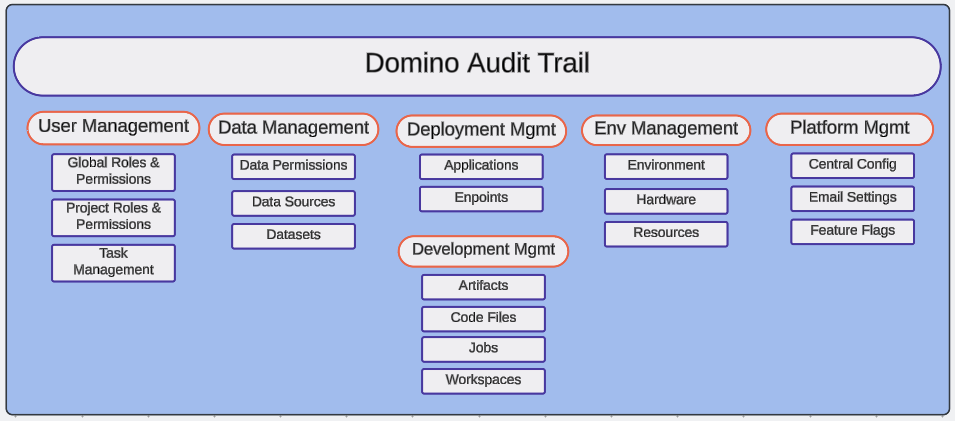
The Unified Audit Trail provides a clear record of important user actions to support compliance and regulatory standards. It tracks key events like dataset updates, project setups, user role changes, and data access, ensuring accountability and data integrity. With features like dynamic search and sorting, it’s easy to use and requires no programming knowledge. Examples of audit trail events include:
-
Added Collaborator
-
Updated User Role
-
Created Dataset
The Unified Audit Trail Data Glossary has a complete list of Events that are captured within the unified audit trail.
The audit trail interface can be opened only by the following roles: SysAdmin or GovernanceAdmin.
Domino can also help customers access System Logs. These system logs are different than the Unified Audit Trail; they capture detailed events primarily used for debugging, troubleshooting, and monitoring performance. Examples of system logs include:
-
Execution logs from user code running as Jobs or Workspaces
-
Kubernetes service logs
-
Detailed Login and Logout Activity
Exploring these logs typically requires skills in log management tools such as Splunk, scripting such as Python, and querying languages, like SQL. Familiarity with cloud systems and platforms like Kubernetes is also usually required.
-
Create filters and view audit events with a dashboard for flexible search options, quick insights, and detailed historical analysis.
-
Export audit trail data using the Audit trail API. The data is JSON but can be parsed and stored in other formats, like CSV.
-
The Audit trail data glossary contains Domino audit event names along with their descriptions.
