Domino can synchronize Domino administrative user roles and organization membership with attributes in your SAML identity provider. Use this to externalize management of these roles and memberships to the identity provider.
The SAML provider application connected to Domino must include group membership as a multi-valued attribute.
To enable this feature, you must update the Configuration key setting authentication.oidc.externalOrgsEnabled to true, then restart Domino services.
Group synchronization attributes
You must include the following attributes if you synchronize groups in Domino.
-
Domino Organizations
-
Name: Can be any name since Domino can map attributes.
-
Multi-valued: Yes
-
Values: One or more of the groups the user belongs to in your centralized identity provider. For any groups specified here, the user will be automatically enrolled in a Domino organization with the same name.
-
Example:
<saml2:AttributeStatement xmlns:saml2="urn:oasis:names:tc:SAML:2.0:assertion">
<saml2:Attribute Name="DominoOrganizations">
<saml2:AttributeValue>nyc-data-scientists</saml2:AttributeValue>
<saml2:AttributeValue>all-data-scientists</saml2:AttributeValue>
<saml2:AttributeValue>sensitive-claims-users</saml2:AttributeValue>
</saml2:Attribute>
</saml2:AttributeStatement>Attribute mapper
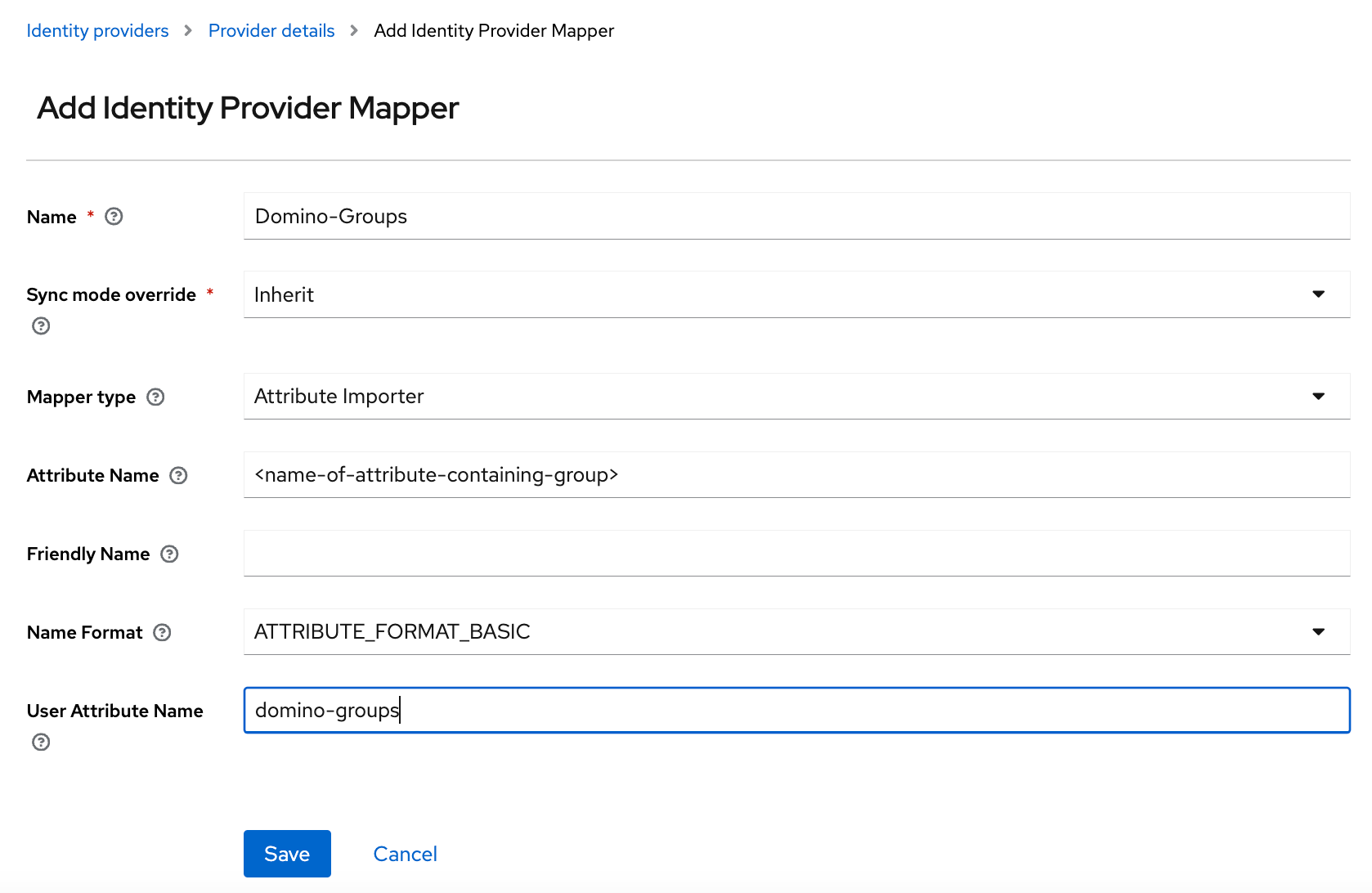
Add an Attribute Importer mapper to the provider configuration in Keycloak.
-
Name: Domino Groups
-
Mapper Type:
Attribute Importer -
Attribute Name: Name attribute for the element that contains the groups for the user.
-
Friendly Name:
FriendlyNameattribute for the element that contains the groups for the user. -
User Attribute Name:
domino-groups.
In addition to group membership, you can also automatically assign Domino administrative and/or user roles to users based on attributes from your SAML identity provider.
Attribute mapper
You must add an Attribute Importer mapper to the provider configuration in Keycloak:
-
Name: Domino System Roles.
-
Mapper Type:
Attribute Importer. -
Attribute Name: Name attribute for the element that contains the Domino system roles for the user.
-
Friendly Name:
FriendlyNameattribute for the element that contains the groups for the user. -
User Attribute Name:
domino-system-roles.
To see the Mappers, go to Clients > domino-play > Client Scopes > domino-play-dedicated.
Domino system roles are controlled by the user’s membership in a set of special user groups in Keycloak. When the user is added or removed from such a group, the role change is propagated to Domino either on the next login or, if the user is currently logged in, within a few minutes (5 minutes by default).
When the user’s SAML token carries the role information as described above, the group membership will be updated automatically.
The administrator can change the user roles from the Admin User management page, but it will be overwritten on the next SSO login if the Domino System Roles mapper is enabled.
Enable Flows
For customers who already have SSO and External Role Sync enabled, an authenticator has been added to Keycloak when upgrading to Domino 5.7.0. For customers with SSO enabled, but External Role Sync disabled, the authenticator is not being added to the Authentication Flows when upgraded to 5.7.0.
For existing customers who don’t have the External Role Sync but now want to enable it, the following manual actions must be taken in the Keycloak UI:
-
Add a new execution to the Domino First Broker Login flow:
-
Navigate to Authentication > Flow details > Domino First Broker Login, then click the Add step button.
-
Search for
Role Group Assignerthen select the Domino Role Group assigner step. Click Add. -
Mark the new Domino Role Group assigner execution as
Required.
-
-
If the
Domino Post Loginauthentication flow doesn’t exist, create it:-
Navigate to Authentication > Flow details > Domino Post Login, then click the Add step button.
-
Search for
Role Group Assignerthen select the Domino Role Group assigner step. Click Add. -
Mark the new Domino Role Group assigner execution as
Required.
-
-
Add the new flows to the Identity providers configuration:
-
Navigate to Identity providers.
-
Next to First login flow override, select
Domino First Broker Loginfrom the list. -
Next to Post login flow, select
Domino Post Loginfrom the list.
-
Learn how to propagate AWS credentials.